In Washington, pretty much everyone agrees that private sector job growth comes mostly from small businesses. Every president since Ronald Reagan has echoed this proposition in a major speech, supported by literature showing an inverse relationship between job growth and firm size dating back to 1979. However, according to Haltiwanger, Jarmin, and Miranda, this popular maxim of economic policy just isn’t true. The authors employ a novel dataset from the Census Bureau to find that when controlling for firm age there is “no systematic relationship between net growth rates and firm size.” For the visual learners among us, the adjustment looks like this:
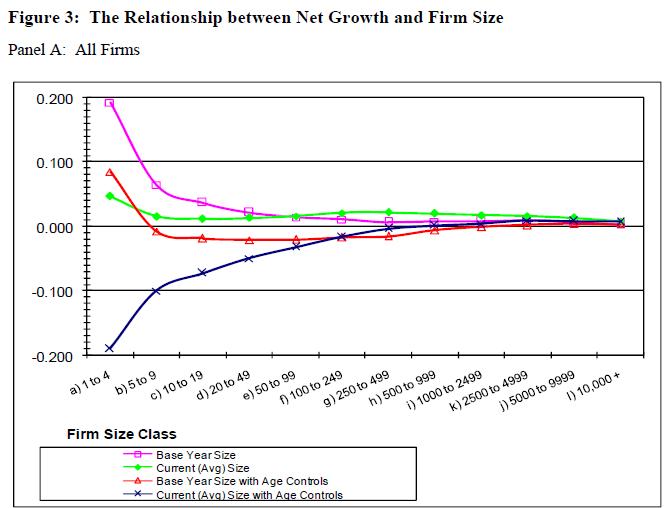
The pink and green lines plot results that might be expected from popular wisdom, while the red and blue lines are gleaned from regressions incorporating a variable for firm age. The results differ based on whether firms are classed by their size in a base year or by the current-year average (we’ll spare you the full methodology but note that the authors prefer the latter). Under either classification the famed inverse relationship is upended upon factoring in age.
As TPI’s Scott Wallsten points out in a recent commentary, measurement difficulties confound economic analysis of high tech markets. Haltiwanger, Jarmin, and Miranda show that even metrics as banal as firm age can cast orthodox understandings across all business sectors into doubt when better data become available.
(Click through to the full post to see the abstract and link for this paper and over 30 others on green tech, the developing world, cyber security, and more.)
Wireless and Spectrum
Kevin W. Caves
“For the better part of a decade, a steadily increasing share of US consumers have eschewed wireline telephony, relying instead on wireless voice service. Yet the existing empirical literature, which has largely utilized data from the turn of the millennium, provides scant evidence of economically significant intermodal cross-price effects (as competition authorities have observed). Using state level panel data from recent years, we estimate a demand system for wireless and wireline service. We estimate positive and economically significant cross-price elasticities, thereby corroborating econometrically a hypothesis that has long been suggested by academics, regulators, and the aggregate data.”
Anindya Ghose, Sang Pil Han
“We quantify how users’ mobile Internet use is related to some unique characteristics of the mobile Internet space like usage-based data pricing, the extent of their geographical mobility and their social network behavior. We use a unique panel dataset consisting of individual-level mobile Internet usage data encompassing their multimedia content uploading and downloading behavior along with detailed data on their voice and text calls, and demographics.”
Thomas Casey
“A tremendous growth in wireless traffic volumes and a shortage of feasible radio spectrum has led to a situation where the old and rigid spectrum regime is not a viable option for spectrum management and a shift towards a more market driven approach has begun. Great uncertainty still exists over how such a radio spectrum market will come about and what kind of shape it would take. This paper studies some long term macro level evolution possibilities for how this radio spectrum market could emerge and what would be the corresponding value chain configurations.”
Ewan Sutherland
“This paper examines how issues concerning international mobile roaming have been addressed in Asia and the Pacific Islands by governments, regulators and operators. The complaints of consumers and business users have been that rates are too high, a problem accentuated by a small number of incidents of “bill shock” in which customers are invoiced for thousands of dollars. Prices have remained high, despite generally supposed competition in mobile markets (e.g., no change in Australia-New Zealand roaming rates between 2007 and 2010). Often information about prices is difficult to obtain or overly complex for customers.”
Broadband
Marc Bourreau, Joeffrey Drouard
“In this paper we study how a phase of service-based competition during which a new entrant operator leases access to an incumbent operator’s network affects the entrant’s incentives to build an alternative infrastructure. In line with the “stepping stone” and “ladder of investment” arguments, we build a framework in which the phase of service-based competition allows the entrant to step into the market by progressively acquiring market experience and market shares. We show that, contrary to conventional wisdom, the acquisition of market experience in a phase of service-based competition may delay facility-based entry, when the prospects for facility-based entry are good. We also show that when the acquisition of experience depends on the entrant’s current customer base, increasing the access charge can retard facility-based entry.”
Paola Garrone, Michele Zaccagnino
“This paper means to add to empirical research on the relationship between competition and firm-level investments in communication networks and services. We explore the moderating action of two measures that can accompany market competition, i.e. privatization and promotion of service-based competition. In addition, we investigate the linearity of the impact of competition on investment, i.e. whether market rivalry fosters investment only under a threshold level (i.e. rivalry escape effect). The empirical analysis is carried out on a sample of incumbents from 28 OECD countries (1993-2008 period)…. Aggregate investment exhibits a highly country specific pattern. No strong causality linkages have been found between stand-alone reform and firm level investment. Neither privatization nor competition in isolation play a significant role. The most relevant explaining factor has been found to be service based competition, which is likely to reduce the incumbent’s incentives to invest, unless a certain degree of rivalry has already emerged in the markets, especially in fixed communications.”
Rob Frieden
“This paper will explain how the FCC has backed itself into a corner in light of its predisposition to apply the information service classification indiscriminately and its perceived duty to make either/or determinations about services, i.e., to apply either the telecommunications service classification singularly, or the information service singularly to a convergent service that combines both elements. The paper also will provide recommendations on how the Commission might recognize that convergent services, such as Internet access, combine both components in much the same way as wireless cellular telephone companies offer both regulated common carrier telecommunications services, subject to forbearance, and unregulated information services via the same conduit. The paper recommends that in light of the ascending importance of Internet access and the lack of sustainable competition that would favor self-regulation, Congress should amend the Communications Act to authorize the FCC to apply limited elements of Title II safeguards as already exists for wireless telephony. In light of the failure of Congress to reach consensus, the paper suggests that the FCC safeguard consumers when information service providers cause harm as the Commission did when a DSL service provider blocked access to competing VoIP services.”
Privacy and Security
Max Stul Oppenheimer
“[A] different class of consent has emerged, typified by computers accepting Internet cookies, where the action underlying the alleged consent is taken not by a human but by a computer … Nothing in traditional consent analysis precludes consent communicated through a computer. However, the underlying question of whether there was intent to manifest consent is more complicated when there is a computer intermediary and involves a determination of whether the action was initiated, or at least acquiesced in, by the human who is alleged to have given consent.”
Paolo Balboni
“[S]ecurity, privacy and legal matters represent the main obstacles that are encountered when implementing cloud computing, because the market provides only marginal assurance. This paper briefly describes the main legal issues related to cloud computing and then focuses on data protection and data security, which are by far the biggest concerns for both cloud service providers (CSPs) and (potential) customers.”
John G. Palfrey Jr.
“In this article, I describe the role of technology and its use in limiting access to knowledge during four phases of development of the Internet. The possibilities associated with how people are using technology to strengthen democracies around the world make up an equally important part of the story.”
Duncan B. Hollis
“This Article challenges the sufficiency of existing cyber-law and security. Law cannot regulate the authors of cyberthreats because anonymity is built into the very structure of the Internet. As a result, existing rules on cybercrime and cyberwar do little to deter. They may even create new problems, when attackers and victims assume different rules apply to the same conduct. Instead of regulating bad actors, this Article proposes states adopt a duty to assist victims of the most severe cyberthreats. A duty to assist works by giving victims assistance to avoid or mitigate serious harms. At sea, anyone who hears a victim’s SOS must offer whatever assistance they reasonably can. An e-SOS would work in a similar way.”
Joanna Kulesza
“This article discusses international law mechanism allowing to prosecute a state for electronic threats generated from its territory, directed against a foreign sovereign. It analyses the possibility to recognize a cyber-attack as an act of international aggression and shows existing difficulties at the present state of international debate. Afterwards, it turns to the traditional notion of state responsibility for the lack of due diligence as a source of state’s responsibility for cyber-attacks. Such due diligence should be guaranteed through sufficient criminal law regulations that are properly executed in order to effectively prevent and persecute electronic attacks. The article submits in this context that an international debate, resulting in international guidelines is required.”
Tech and the Developing World
Jenny C. Aker, Isaac M. Mbiti
“We examine the growth of mobile phone technology over the past decade and consider its potential impacts upon quality of life in low-income countries, with a particular focus on sub-Saharan Africa….While current research suggests that mobile phone coverage and adoption have had positive impacts on agricultural and labor market efficiency and welfare in certain countries, empirical evidence is still somewhat limited. In addition, mobile phone technology cannot serve as the “silver bullet” for development in sub-Saharan Africa.”
Arzak Khan
“The transition from analog to digital cable network presents enormous challenges for a developing country like Pakistan where 78 per cent household’s access to information and entertainment services is through this medium. This article gives an in depth overview of the prevalent market trends on the adoption of digital TV from the point of view of consumers who are expected to bear the cost of converting their household TV from analog to digital but have very little say in its policy making and regulation.”
Raphael Bergoeing Sr., Norman Loayza, Facundo Piguillem
“This paper explores how developmental and regulatory impediments to resource reallocation limit the ability of developing countries to adopt new technologies. An efficient economy innovates quickly; but when the economy is unable to redeploy resources away from inefficient uses, technological adoption becomes sluggish and growth is reduced. The authors build a model of heterogeneous firms and idiosyncratic shocks, where aggregate long-run growth occurs through the adoption of new technologies, which in turn requires firm destruction and rebirth. After calibrating the model to leading and developing economies, the authors analyze its dynamics in order to clarify the mechanism based on firm renewal. The analysis uses the steady-state characteristics of the model to provide an explanation for long-run output gaps between the United States and a large sample of developing countries. For the median less-developed country in the sample, the model accounts for more than 50 percent of the income gap with respect to the United States, with 60 percent of the simulated gap being explained by developmental and regulatory barriers taken individually, and 40 percent by their interaction. Thus, the benefits from market reforms are largely diminished if developmental and regulatory distortions to firm dynamics are not jointly addressed.”
Net Neutrality
Eitan Altman, Pierre Bernhard, George Kesidis, Sulan Wong, Julio Rojas-Mora
“Hahn and Wallsten wrote that net neutrality ‘usually means that broadband service providers charge consumers only once for Internet access, do not favor one content provider over another, and do not charge content providers for sending information over broadband lines to end users.’ In this paper we study the implications of being non-neutral, particularly by charging the content providers. Using game theoretic tools, we show that by adding the option for the service providers to charge the content providers, not only may the content providers and the internauts suffer, but also the access provider’s performance degrades.”
Kenneth R. Carter, Tomoaki Watanabe, Adam Peake, J. Scott Marcus
“In this paper, we compare and contrast the regulatory approaches to addressing Network Neutrality in three countries which represent three roughly different approaches.”
J. Scott Marcus
“Following Comcast vs. FCC, there have been efforts in the U.S. Congress to change U.S. law to ensure that the FCC has the necessary authority to implement these programs. Meanwhile, Chairman Genachowski has proposed a sweeping re-thinking of the regulatory policy of the past ten years, the Third Way, that seeks to strengthen the underpinnings of the FCC’s authority under existing law. Either approach represents a major re-thinking of current policy, and either is likely to have unforeseen consequences. This paper seeks to elucidate the implications of such a change.”
Tech and Macroeconomics
John Haltiwanger, Ron S. Jarmin, Javier Miranda
“There’s been a long, sometimes heated, debate on the role of firm size in employment growth. Despite skepticism in the academic community, the notion that growth is negatively related to firm size remains appealing to policymakers and small business advocates. The widespread and repeated claim from this community is that most new jobs are created by small businesses. Using data from the Census Bureau Business Dynamics Statistics and Longitudinal Business Database, we explore the many issues regarding the role of firm size and growth that have been at the core of this ongoing debate (such as the role of regression to the mean). We find that the relationship between firm size and employment growth is sensitive to these issues. However, our main finding is that once we control for firm age there is no systematic relationship between firm size and growth. Our findings highlight the important role of business startups and young businesses in U.S. job creation. Business startups contribute substantially to both gross and net job creation. In addition, we find an “up or out” dynamic of young firms. These findings imply that it is critical to control for and understand the role of firm age in explaining U.S. job creation.”
John Gibson. David McKenzie
“Brain drain has long been a common concern for migrant-sending countries, particularly for small countries where high-skilled emigration rates are highest. However, while economic theory suggests a number of possible benefits, in addition to costs, from skilled emigration, the evidence base on many of these is very limited. Moreover, the lessons from case studies of benefits to China and India from skilled emigration may not be relevant to much smaller countries. This paper presents the results of innovative surveys which tracked academic high-achievers from five countries to wherever they moved in the world in order to directly measure at the micro level the channels through which high-skilled emigration affects the sending country. The results show that there are very high levels of emigration and of return migration among the very highly skilled; the income gains to the best and brightest from migrating are very large, and an order of magnitude or more greater than any other effect; there are large benefits from migration in terms of postgraduate education; most high-skilled migrants from poorer countries send remittances; but that involvement in trade and foreign direct investment is a rare occurrence.”
Dorota Dobija, Karol Marek Klimczak, Narcyz Roztocki, Heinz Roland Weistroffer
“[T]his study examines stock market reactions to announcements of information technology investments in Poland, an emerging market and transition economy. Based on 68 announcements by companies traded at the Warsaw Stock Exchange in the period 2002 to 2009, our study confirms some previously published results, but also shows that specific characteristics of announcements play a more important role than has been commonly assumed.”
Raphael Kaplinsky
“This paper overviews the history of standards, explains the difference between different types of standards, and identifies the key stakeholders involved in the setting of standards. It then addresses the role that standards play in enterprise upgrading and considers some of the major costs for producers in meeting standards, including potential cost barriers for small-scale producers. Before concluding with a discussion of the policy challenges raised by these developments, it discusses the extent to which standards intensity in global value chains will be affected when the final markets increasingly move from high-income consumers in the North to lower-income consumers in Southern economies such as China and India.”
Competition and Antitrust
Stephen M. Maurer
“Modern open source (“OS”) software projects are increasingly funded by commercial firms that expect to earn a profit from their investment. This is usually done by bundling OS software with proprietary goods like cell phones or services like tech support. This article asks how judges and policymakers should manage this emerging business phenomenon. It begins by examining how private companies have adapted traditional OS institutions in a commercial setting. It then analyzes how OS methods change companies’ willingness to invest in software.”
Antonio Sciala, Fabio M. Manenti
“This paper presents a model of competition between an incumbent and an entrant firm in telecommunications. The entrant has the option to enter the market with or without having preliminary invested in its own infrastructure; in case of facility based entry, the entrant has also the option to invest in the provision of enhanced services. In case of resale based entry the entrant needs access to the incumbent network. Unlike the rival, the incumbent has always the option to upgrade the existing network to provide advanced services. We study the impact of access regulation on the type of entry and on firms’ investments. Without regulation, we find that the incumbent sets the access charge to prevent resale based entry and this overstimulates rival’s investment that may turn out to be socially inefficient. Access regulation may discourage welfare enhancing investments, thus also inducing a socially inefficient outcome. We extend the model to account for negotiated interconnection in case of facilities based entry.”
Economics of the Internet
Dirk Bergemann, Alessandro Bonatti
“We develop a model with many advertisers (products) and many advertising markets (media). Each advertiser sells to a different segment of consumers, and each medium has a different ability to target advertising messages. We characterize the competitive equilibrium in the media markets and evaluate the implications of targeting in advertising markets. An increase in the targeting ability leads to an increase in the total number of purchases (matches), and hence in the social value of advertising. Yet, an improved targeting ability also increases the concentration of firms advertising in each market. Surprisingly, we then find that the equilibrium price of advertisements is first increasing, then decreasing in the targeting ability. We trace out the implications of targeting for competing media. We distinguish offline and online media by their targeting ability: low versus high. As consumers, relative exposure to online media increases, the revenues of offline media decrease, even though the price of advertising might increase.”
Intellectual Property
Kimberley Isbell
“[F]or all of the heated rhetoric blaming news aggregators for the decline of journalism, many are still left asking the question: are news aggregators violating current law? This white paper attempts to answer that question by examining the hot news misappropriation and copyright infringement claims that are often asserted against aggregators, and to provide news aggregators with some “best practices” for making use of third-party content.”
Eitan Altman, Sulan Wong, Julio Rojas-Mora
“Recent publications have reached conflicting conclusions on whether allowing users to have unlimited free access for downloading music and films is beneficial or not for the content production industry (CPI). Not only do models differ in their conclusions, but there has also not been an agreement on the validity of data on the impact of free access to music and films using P2P on the profits of the CPI and on the demand for CDs and DVDs. We provide in this paper a model that allows to study this question using elementary mathematical tools. In particular, it includes the effect of sampling on the willingness to buy. Preliminary numerical experiments show that benefits are maximized by avoiding any control measures against unauthorized sampling over P2P networks.”
Sulan Wong, Eitan Altman, Julio Rojas-Mora
“In this paper we describe first some of the ideological roots of free access to the Internet along with its main opponents. We then focus on the problem of “Internet piracy” and analyze the efficiency of efforts to reduce the availability of copyrighted creations that are available for non-authorized free download.”
Niva Elkin-Koren
“The prevalence of social production and the increase in User Generated Content (UGC) destabilize some of the fundamental premises of our current copyright law. Copyright law is primarily designed to regulate the relationships of a single owner with other non-owners and is focused on the sovereignty of the author/owner. Social production, by contrast, requires us to articulate a matrix of relationships between the individual, the facilitating platform and the communities and crowds involved in social production. The transition from industrial production to social production transforms the social relations associated with the production of content and therefore requires adjustment of the institutions that design such relations. This Article closely examines the social dimension of content production and analyzes the consequences for the governance of content in the social web.”
Abby Kweller
“This Article reviews the creation of the Apple iPhone and the function of technological protection measures that are put in place by Apple for various control purposes. It also reviews the process of “unlocking” and “jailbreaking” an iPhone and the legality that rests on this hacking technique.”
Assaf Jacob, Zoe Argento
“This paper explores the legal ramifications of the prevalent Internet Service Provider practice of providing caching services to P2P network users. First, the paper describes the P2P industry, its benefits and drawbacks. Then the paper discusses several caching techniques that can be implemented, and indeed are implemented, by ISPs around the globe. These practices allow ISPs to provide clients with better services but also expose them to copyright infringement suits by third parties. The article will discuss how copyright law should consider the costs and benefits to the public of P2P caching practices, especially in the application of legal doctrines such as direct and indirect infringement and fair use.”
Mark Perry
“This paper shines light into an area of digital content that is often hidden from users: it discusses the background and issues surrounding Rights Management Information, which is widely used as part of a digital rights management strategy by publishers, along with technological protection measures, but it has been little studied in its own right. The World Intellectual Property Organization Treaties specifically address the protection of such information. Rights Management Information in the digital age has the capacity to offer all stakeholders in creative works, from creator to copyright owners and content users, additional control and flexibility over the use and appreciation of a work and dissemination of data about the rights in the content. This paper proposes that the technology available today for increased levels of Rights Management Information be utilized to do more than simply give additional protection for works from illicit exploitation; rather it should also address the protection of transparency, completeness, privacy and freshness in the information that is attached to works.”
Green Tech
Orada Teppayayon, Erik Bohlin, Simon Forge
“The environmental issue has generally received much attention from the public for decades, especially as a result of heavy industry – electrical energy, oil and gas, mining, steel and metals. Recently, attention has been paid to Information and Communication Technology (ICT) and its effect on the knowledge and related industries. Broadband, both fixed and mobile, is not an exception. Even though it has been recognized as a factor that has contributed to social and economic development, a negative effect can also be seen in particular regarding the environment. This paper provides a review of how government policy, in particular by the EU and Japan, are moving towards the transition to sustainability by utilizing ICT, as well as an evaluation of the pros and cons of broadband development.”
John W. Houghton
“Drawing on the existing literature, this paper presents an overview of how the Internet and the ICT and related research communities can help tackle environmental challenges in developing countries.”
Bronwyn H. Hall, Christian Helmers
“Global climate change mitigation will require the development and diffusion of a large number and variety of new technologies. How will patent protection affect this process? In this paper we first review the evidence on the role of patents for innovation and international technology transfer in general. The literature suggests that patent protection in a host country encourages technology transfer to that country but that its impact on innovation and development is much more ambiguous. We then discuss the implications of these findings and other technology-specific evidence for the diffusion of climate change-related technologies. We conclude that the “double externality” problem, that is the presence of both environmental and knowledge externalities, implies that IP may not be the ideal and cannot be the only policy instrument to encourage innovation in this area and that the range and variety of green technologies as well as the need for local adaptation of technologies means that patent protection may be neither available nor useful in some settings.”